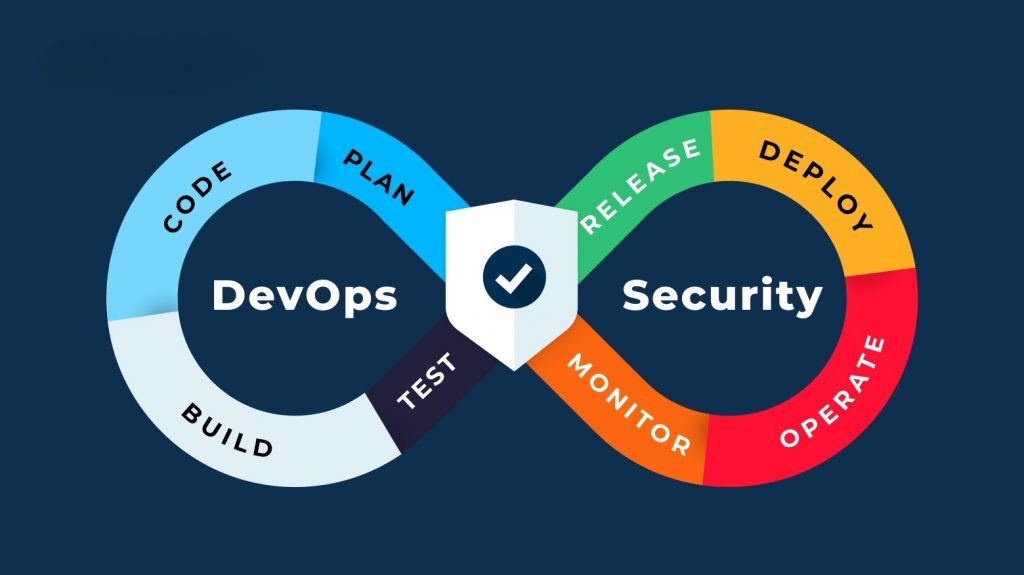
DevSecOps Culture: Integrating Security Throughout the Software Development Lifecycle
Apr 25, 2025 • Hamed Dehongi
In today’s fast-paced software landscape, security can no longer be an afterthought. Waiting until …
Write a blog post about Cybersecurity.

Apr 25, 2025 • Hamed Dehongi
In today’s fast-paced software landscape, security can no longer be an afterthought. Waiting until …

Apr 25, 2025 • Hamed Dehongi
In today’s constantly evolving threat landscape, preventing every cyber incident is virtually impos…

Apr 25, 2025 • Hamed Dehongi
Quantum computing promises to revolutionize fields from materials science to drug discovery by harn…

Apr 25, 2025 • Hamed Dehongi
The shift toward remote and hybrid work models has unlocked new levels of flexibility and productiv…

Apr 25, 2025 • Hamed Dehongi
In an era of stringent privacy regulations, organizations must be prepared not only to prevent data…

Apr 25, 2025 • Hamed Dehongi
In today’s interconnected business landscape, organizations rely heavily on third-party vendors, pa…
Learn how our technology consulting can help your business grow and innovate.
Explore Services